
Since the beginning of 2019, ASIC owners have complained about stolen hash capacities. Hackers infect user’s devices with malware which is programmed to transfer the reward to their workers, bypassing the addresses of the owners. Some hackers manage to earn more than 1 BTC per day only due to the viruses in other people's devices.
Infected ASICs usually come from used or resold devices with pre-installed malware, or from users installing fake “performance boost” firmware that secretly redirects rewards.
The hype of cryptocurrencies could not help but attract hackers. But in the case of a wallet or blockchain it is rather difficult to “hack” it, turns out things are much easier with using the victim’s equipment as a remote miner. In 2018, the growth of hidden mining malware reached 4467% compared with the previous year. However, it affected not only PCs and its hardware (video cards, processors), but specialized mining devices e.g. ASICs as well. In early 2019, a spread of malicious firmware was detected, which offered to Antminer S9 an overclocking potential of 18 Th/s. After activating the firmware, the Trojan virus blackmailer hAnt demanded a ransom of 10 BTC by threatening to overheat the device with its further disruption.
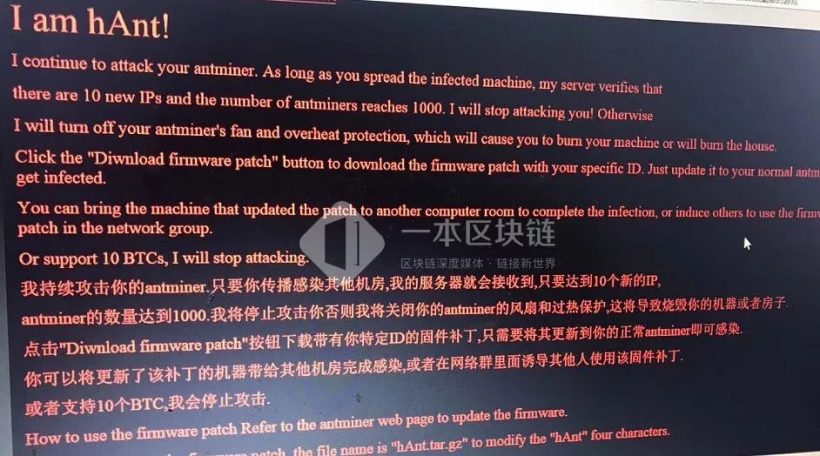 Later, one of the miners with 4 thousand of devices in possession was informed of an unknown virus which had transferred about 8 thousand dollars of bitcoins mined during that day to a third-party address, until the address substitution had been revealed. The user was able to format the system and reflash the ASICs with an SD card, but it took more than four days. He was lucky to promptly disconnect part of the “healthy” machines from the local network. The reason for the whole situation was the custom ASIC firmware.
Later, one of the miners with 4 thousand of devices in possession was informed of an unknown virus which had transferred about 8 thousand dollars of bitcoins mined during that day to a third-party address, until the address substitution had been revealed. The user was able to format the system and reflash the ASICs with an SD card, but it took more than four days. He was lucky to promptly disconnect part of the “healthy” machines from the local network. The reason for the whole situation was the custom ASIC firmware.
All these and new viruses are regularly created and constantly being modified by hackers. Malicious software is becoming harder to detect and more dangerous every day. There is no such thing as invulnerability. No one is 100% protected since after getting into a system, the Trojan quickly spreads to other devices, so it is necessary to restore them manually and individually. In case of ASIC S9 the firmware reflashment has the longest time compared to a standard scanning and curing procedure.
You can tell an ASIC is infected if it connects to unknown mining pools, redirects rewards to a different wallet, or blocks you from changing pool settings and firmware updates.
If you are wondering how to detect crypto mining malware on your devices, the first sign is that an infected ASIC connects to another pool and starts sending the reward to the worker with the address of the hacker's wallet. The address of one of the last recipients exposed is: 3CJgXokLQrRCQcEoftS7MbPDSXhXpX6P55 (more at: https://www.nicehash.com/miner/3CJgXokLQrRCQcEoftS7MbPDSXhXpX6P55). Sometimes ASICs can be infected right from the start after purchasing them from China. The malware is often installed on used models for the purpose of reselling them and further stealing their terahashes. But more often users jump at the bait of performance and profitability acceleration and download the firmware by themselves. Knowing how to detect bitcoin miner virus early is crucial, since this kind of malware usually hides by redirecting rewards and blocking configuration changes.
 Unlike a typical development fee (DevFee) for the firmware usage, this virus is there for 12 hours a day mining for another user, which is 50% of your reward. Rolling back to the standard firmware helps only temporarily since this kind of virus is able to reactivate itself soon and continue sending part of the reward to another user.
Unlike a typical development fee (DevFee) for the firmware usage, this virus is there for 12 hours a day mining for another user, which is 50% of your reward. Rolling back to the standard firmware helps only temporarily since this kind of virus is able to reactivate itself soon and continue sending part of the reward to another user.
By the way, such a trojan will not let you change the address to your own or reset configuration. It also blocks firmware updates. With this method hackers get from 0.5 to 1 BTC per day just by using someone else's equipment. This is 5 - 10 thousand dollars every 24 hours. We can only guess how many devices are already infected and how many will be in future. On such a scale of the "epidemic spread," security measures must be taken into consideration.
In some cases, a simple tool called WinSCP can help if you want to know how to check for crypto mining malware directly on your device. By entering the ASIC address, root name and password. Once you see the structure with files, check the bmminer.conf file in the config folder. If the foreign address mentioned above appears in it (3CJgXokLQrRCQcEoftS7MbPDSXhXpX6P55), it means your device is affected. Pools will also be different. (as in this case, nicehash).
The most reliable way to cure an infected ASIC is to reflash it with official firmware using an SD card, which completely removes the malicious software.
If you’re looking for practical steps on how to remove crypto mining malware, the process usually involves scanning devices with BraiinsOS or other tools, and in some cases resetting the IP address before installing the official firmware.
In some cases with S9 virus, it only takes to reset the IP address and immediately install the official firmware to completely get rid of the malicious one. Anyway, the removal process takes time, requires knowledge and an SD card with a capacity of 2 GB or higher.
Knowing how to get rid of crypto mining malware efficiently can save miners days of downtime, since delays in reflashing or scanning allow the virus to keep spreading across the farm.
First, you need to download the Win32DiskImager tool. Then, insert the SD card into the card reader, run Win32DiskImager and copy the Recovery image for S9 to the memory card.
After preparing the SD card and running Win32DiskImager, you’ll need to perform several steps with the ASIC control board to reinstall the recovery image. This manual reflashing process is essentially how you delete miner virus completely, since it wipes the infected firmware and restores the device to a clean state.
Turn off the power supply to the control board; then disconnect the riser chips;
move the jumper forward (the first one from the ASIC panel and the farthest from the flash drive, usually JP4), insert the card with the image, turn on the power;
then you need to connect the control board, wait for about a minute until a stable periodic indication of the LEDs on the LAN. The first time they should light up upon 20 seconds and then constantly begin to flash for a minute.
This indicates the firmware is being installed. After that, turn off the power, return the jumper to its place and remove the SD card. Then you need to assemble the device. After starting the ASIC, a well-known Bitmain menu should appear, through which you will be able to install the original or custom firmware.
If the whole farm is infected, the fastest solution is to install antivirus firmware that can scan, clean, and protect all ASICs at once instead of reflashing them one by one.
The above method applies when talking about a single device. However, as we know any virus spreads very quickly to all devices. If you have dozens or hundreds of ASICs in use, it will be hard to quickly disconnect them from the network as well as reflashing them one by one.
To help miners choose the most effective approach for dealing with infected ASICs, here’s a comparison of the main solution methods, including their pros, cons, and ideal use cases.
| Method | Best For | Pros | Cons |
|---|---|---|---|
| Manual reflash with SD Card | Single devices (e.g.,Antminer S9) | Full reset (wipes malware completely) | Time-consuming. Requires technical knowledge |
| Reset +official irmware install | Light infections on a few devices | No special tools beyond official firmware. | Doesn’t always work (some malware reactivates) Not effective for persistent trojans. |
| Antivirus firmware (e.g., S9/T9+ solutions) | Large farms (dozens/hundreds of ASICs) | Automates miner virus removal. Built-in malware detection. Extra features (sleep mode, overclocking, AsicBoost). Ongoing protection. | Third-party firmware (must trust the source). May void warranty. Learning curve for setup. |
| Third-party scanners (BraiinsOS, etc.) | Detecting infections across multiple ASICs. | Helps with how to check for crypto mining malware. Good for large networks. | Only detects, doesn’t cure. Still requires follow-up reflashing or firmware change. |
There is a solution represented by a comprehensive firmware for Antminer S9, T9 +, which has the following advantages over manual miner virus removal. It not only automates scanning and cleaning but also provides protection against reinfection:
Built-in antivirus, checking and recognizing the presence of malware. If the device is clean, you can revert back to your original firmware or keep using the downloaded version;
Ability of manual scanning of viruses;
The firmware is located on the site protected with SSL, which excludes the possibility of replacing the file;
It ensures the stability of working devices;
Adds the ASIC "sleep mode" function;
Allows individual chip overclocking;
Allows overclocking and optimization with AsicBoost technology, and etc.
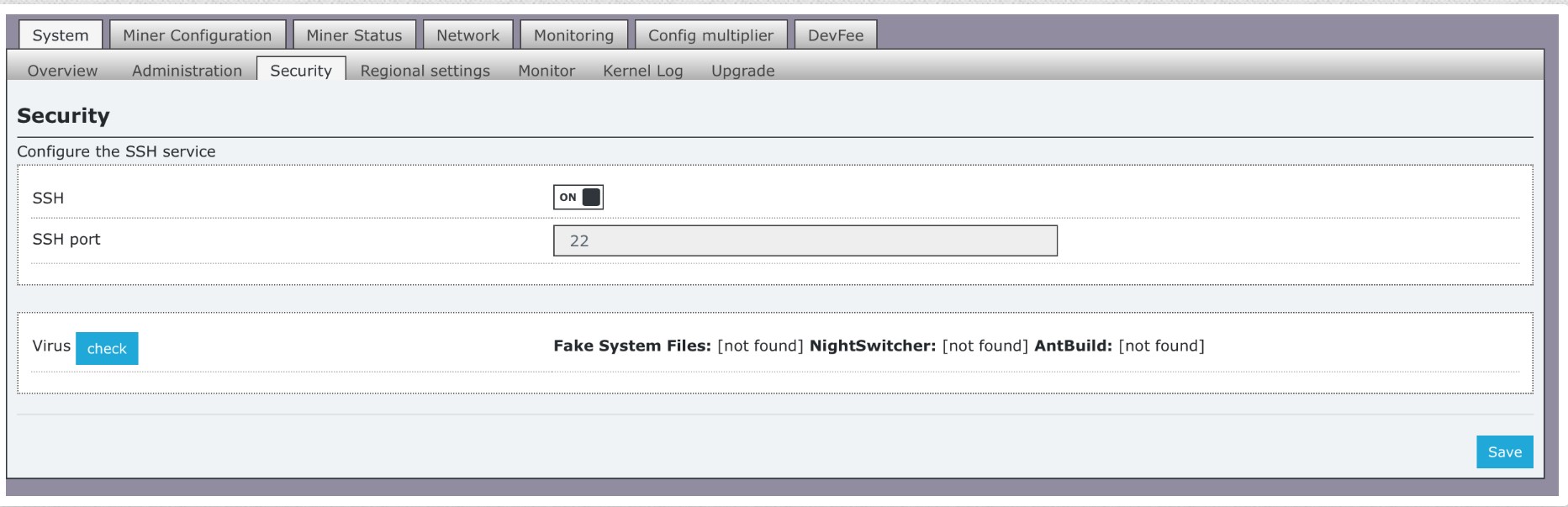
Built-in antivirus allows you to scan your ASIC S9, T9 + for viruses. In order to do this, once the firmware has been installed, navigate to the System > Security tab and press the Virus Check button to enable scanning.
Unlike with hacker products its distinguishing feature is the presence of customer support. Means that you can contact the developers with any questions and get advice. To guarantee stable and profitable mining without sharing the reward with anyone you must download the original firmware for ASIC from the official website.
If your ASIC is infected, it usually connects to a strange mining pool and sends your rewards to someone else’s wallet. You can use tools like WinSCP or special scanners to check the settings file and see if an unknown pool address is there.
Watch your miner’s performance. If hashrate drops or rewards look lower than normal, it can be a sign. You can also open the config file to check pools or use antivirus firmware that scans devices on your network.
Some viruses block you from changing pools or updating firmware. If you see that you can’t edit settings, or your rewards keep disappearing, your ASIC might be infected.
The safest way is to reflash the device with official firmware. You do this by copying the recovery image to an SD card and reinstalling the system. This clears the malware completely.
They mean almost the same thing. “Malware removal” usually means cleaning the software, and “virus removal” often means reinstalling firmware to wipe the infection.
If you have many ASICs, fixing them one by one takes too long. It’s better to use special antivirus firmware that can scan, clean, and protect all devices at once.